Authentication Is Used for Which of the Following Purposes
Which of the following is NOT an authentication method used by SSH. View the full answer.

Top 10 Two Factor Authenticator 2fa Apps For Android In 2021 Cyber Security Cyber Security
Lets review the 4 most used authentication methods used today.
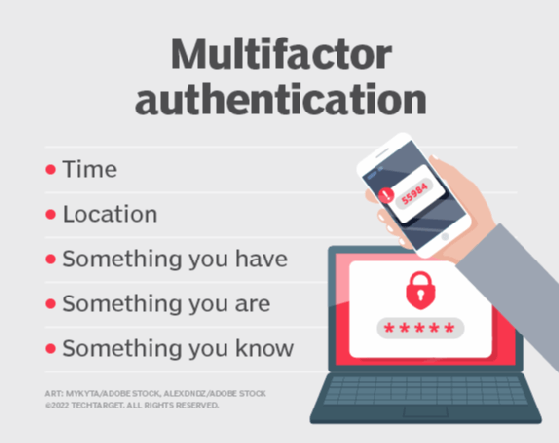
. Authentication means proving who you are for example with a usernamepassword combination and includes all of the methods described in the Authentication section below. Well use a small library for the signingvalidation of the cookies which basically contains the code used by the Play framework for this specific task. To perform authentication with the help of the requests module we can use the HTTPBasicAuth class from the requests library.
Experts are tested by Chegg as specialists in their subject area. Smart card logon authentication. Who are the experts.
The collected data might include the start and stop connection times. Granted access to authorized Application Directories. Navigate to System Authentication Advanced Policies Policy.
Therefore it does not send passwords across the network and it safeguards stealing passwords across the network. OAuth2 An internally configured swagger-api client is used to obtain a JWT. The TSec project provides an authentication and authorization module for the http4s project 018-M4.
Cisco provides two common methods of implementing AAA services. Once that is done authorization verifies their permission level. HTTP Authentication Schemes Basic Bearer The HTTP Protocol also defines HTTP security auth schemes like.
The transport is HTTPS or the destination is in the TrustedHosts list and explicit credentials are provided. Users have the option to authorize with the following options. It is the process of confirming the identification of a user or in.
Block or throttle any requester who exceeds the rate limits. Case class User id. Authentication seeks to validate the identity of a user.
Track who is making the requests. Types of Authentication Azure Communication Services has three types of Authentication theyre used for different purposes. The authentication object is offered to the auth parameter of the get method.
We review their content and use your feedback to keep the quality high. This class accepts two parameters a username and a password. For our purposes here we will use the following definition.
Use smart cards to authenticate users to Citrix Virtual Apps and Desktops servers. Default authentication may be used with an IP address under the following conditions. Enter a name for the policy select the server that you created in the previous steps.
In this case InsuranceNow is the identity provider. JWT An Okta-provided JWT provides authentication. Question 44 2 pts.
Apply different permission levels to different users. Use the following commands as a reference to configure log on for a group. Granted access to authorized data.
SQL Server does not store the users credentials. This identification process verifies a users identity usually through something they know such as a password something they have such as an ID card or USB token or something they are via biometrics. Basic authentication A valid InsuranceNow username and password provide authentication.
Then based on their user ID or role and group they are. AAA Authentication can be used to authenticate users for administrative access or it can be used to authenticate users for remote network access. Track usage of the API.
To configure LDAP authentication on the Citrix ADC appliance for management purposes by using the CLI. Once smart card support is enabled for both the server and Citrix Workspace app provided the application policy of the smart card certificates allow it you can use smart cards for the following purposes. Authentication is an absolutely essential element of a typical security model.
TACACS Terminal Access Controller Access Control System is an older authentication protocol common to UNIX networks that allows a remote access server to forward a users logon password to an authentication server to determine whether access can be allowed to a given system. Although authentication and authorization work in combination there are differences in meaning and purpose. For example authentication is necessary for a user to enter the company database but authorization is what decides what information they are allowed to view and change.
αὐθεντικός authentikos real genuine from αὐθέντης authentes author is the act of proving an assertion such as the identity of a computer system user. Access Key authentication is suitable for applications running in a trusted service environment. Authentication is used in computer security and user access management systems.
In contrast with identification the act of indicating a person or things identity authentication is the process of verifying that identity. Connecting to remote server failed with the following. Smart card application support.
On Windows a thread is. Overall authentication and authorization with APIs serves the following purposes. TACACS is an encryption protocol and therefore less secure than the.
This class represents an HTTP Basic Authentication and it is attached to a request. Kerberos Client Certificate Authentication and Smart Card Authentication are examples for mutual authentication mechanismsAuthenticationis typically used for access control where you want to restrict the access to known usersAuthorization on the other hand is used to determine the access levelprivileges granted to the users. This article discusses about an error message generated when configuring AppInsight for IIS on nodes.
Authenticate calls to the API to registered users only. Windows authentication is a secure way of connecting to SQL Server and it uses the tokens and SPNs for authentication purposes using the Kerberos authentication protocol. 4 Most Used Authentication Methods.
Access Key authentication for SMS Network Traversal Call Automation Identity and access token operations. Authorization means proving your right to access a given resource. The purpose of this security checkpoint is to ensure that authenticated users are granted access to the Reporting Server.
This data can be used for such purposes as auditing or billing.

Certificate Template 802 1 Templates Example Templates Example Certificate Templates Templates Professional Templates
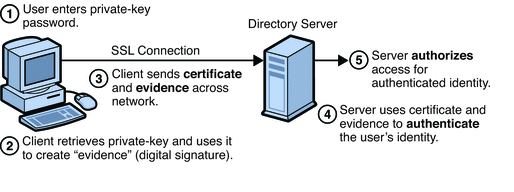
Introduction To Certificate Based Authentication Sun Directory Server Enterprise Edition 7 0 Reference

Belum ada Komentar untuk "Authentication Is Used for Which of the Following Purposes"
Posting Komentar